
The Great Aviation Tablet War


The previous two installments of this three-part series on tablet computers in the aviation world covered the operating systems (Apple’s iOS versus Google’s Android versus Microsoft’s Windows 8) and the software applications (app) market. We will discuss security issues facing tablet use and the apps/data in aircraft to wrap this up.
The Virtual World is a Treacherous One
There is a news release on this topic practically every day — hacked credit cards, hacked payment systems, malware affecting some sensitive computer systems, stolen laptops that contain databases of peoples’ social security numbers, Nigerian princes offering to share their bounty with you (as long you provide your credit card to expedite the cash transfer), etc. Scary stuff indeed.
There is a raging debate amongst IT and cybersecurity experts on which of these platforms is the most secure, and very little agreement. If you are a tablet computer user (especially an Apple iPad user), you are much less at risk than those poor souls who use traditional desktop computers (with the caveat that if you are taken in via an e-mail phishing or some type of malicious scam). Google and Microsoft have also improved their security in recent software versions of their operating systems, but due to the ‘walled garden’ that Apple forces users into via the iTunes store, a degree of safety is provided to end users.
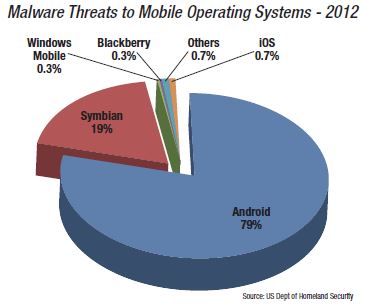
According to a report from the U.S. Department of Homeland Security in July 2013, Android is the world’s most widely used mobile operating system and continues to be a primary target for malware attacks due to its market share and open source architecture. Industry reporting indicates that 44 percent of Android users are still using older versions of the operating system.These have a number of security vulnerabilities that were fixed in later versions. The chart published by the DHS clearly identifies which mobile operating systems were targeted more often.
Securing yourself and your data on any device requires that you not only keep your devices’ software updated, but also that you are aware of how you communicate (secured WiFi, cellular, Bluetooth) and what types of trusted apps you download. As you can tell from the DHS chart, the underlying operating system plays a large part in how vulnerable your tablet might be.
Background on the Tablet’ Operating Systems
Both the Apple iPad and each of the Google Android-compliant tablets use what is referred to as a mobile operating system (OS), which is a set of software that operates tablet computers, smartphones or other mobile devices. Such mobile OS utilize many features of a typical personal computer operating system with mobile device capabilities and features such as touchscreen user interfaces, wireless connectivity (via Bluetooth, cellular and Wi-Fi), GPS mobile navigation, cameras, voice recording and audio playback, among other functions. Traditional desktop computer OS had significantly more capabilities than the early mobile device systems, but this is no longer true. In recent years, the OS development for phones has progressed towards bridging the gap between desktop and mobile. The differences between these OS have become less significant.
The positive side of this evolution is that tablets will continue to see more applications that were originally designed for desktop PC use migrate over (after major redevelopment efforts by software providers). This will further shift sales of desktop and laptop computers to smaller tablets.
The negative aspect of this is that cyber security issues might also follow from the desktop world to some degree. Tablets (and smartphones) are generally less prone to cyber attacks and malware due to their more constrained memory, software design and use, and how app downloads are tightly constrained (at least by Apple) — but this should not lull us into inaction.
Let’s take a look at how secure each of the tablet families really is.
Apple iOS Security
iPads (and iPhones) are generally considered to be among the most secure devices available today. They have their issues and critics of Apple often point out their slow responses to patch identified cyber risks. Even so, iOS has been tested by the U.S. Air Force, commercial airlines and operators and others, and has been approved for use (with caveats). Bill Blanchette, a security researcher who has investigated iPads in the commercial and Air Force domains, states that: “iPads have a robust security architecture, including hooks for certificate usage, baked in. The issue surfaces in the implementation decisions BYOD provides less control over the devices where a more comprehensive security architecture can be imposed at the cost of maintaining a fleet of iPads. The biggest thing I have seen is maintaining the integrity of the iOS/security architecture, jailbreak the tablet and the gates are wide open for anyone.”
In fact, Apple has not approved any antivirus apps for inclusion in the iTunes store. The only security-related apps are for virtual private networks (VPNs) (to secure web browsing and data transfers) and encrypted e-mail and messaging, which gives iOS users the impression that typical desktop PC security software in not needed. Perhaps Apple has a strong case on this, since there have been few (known) successful cyber attacks on iPads and iPhones.
John Zimmerman, vice president at Sporty’s Pilot Shop and publisher of the iPad Pilot News (ipadpilotnews.com), states that, “As far as security, I really haven’t seen or heard of many issues. One of the reasons people love/hate Apple is the tight control the App Store process demands. While that’s a pain for app developers (including us), it does improve the quality of apps and prevents most spyware from making it in.”
They are not without their security flaws, but, due to a number of reasons outlined below, has a good degree of security:
1. According to Apple, it designed the iOS with security at its core. The latest version supports single sign on (important for corporate users), data encryption and built-in biometric authentication.
2. Apple’s iPad memory design is constructed to minimize the harm that could be done by malware, and each app is constrained to operate in its own ‘sandbox’. This effectively mitigates the risk that other apps or stored data can easily be compromised.
3. As mentioned earlier, Apple uses a ‘walled garden’ approach to the iTunes store, which is the only way for individual users to download apps. Corporate users who use Apple’s enterprise solutions to manage business iOS devices have much more control on how iPads are managed and secured by the organization. As an example of this, Apple allows IT administrators to fully control and configure via iOS configuration profiles that allow administrators to pre-setup connections to your company’s e-mail system or to pre-setup connections to your company’s secure Wi-Fi networks, but also restrict the device in many ways including preventing access to the iTunes App Store, or the Safari browser.
Apple has been morphing iOS away from a basic consumer-focused mobile OS to a secure, mature OS that can handle the needs of governments and companies.
Google Android Security
If you look at the DHS chart earlier in this article, you might be thinking ‘what security?’ This would be an unrealistic assumption. Android has security and a majority of its problems are self-inflicted by its open-source nature, the ability to only download apps from other web sites besides the official Google Play store, and how Google allows hardware vendors to keep their devices on older versions of the OS.
Android devices can also be secured effectively. Google has boosted its support for many of the security features that Apple espouses, but some of this depends upon which tablet manufacturer’s product you have chosen. Samsung has been integrating its hardware with Android security mechanisms and has launched its secure mobile OS (which is heavily linked into Android), Samsung KNOX. The capabilities of KNOX compete effectively with the latest iOS and Windows capabilities. In general, Android is seemingly not as secure as iOS, but it is comparable if corporate users use the Samsung KNOX software.
Microsoft Windows 8 Security
From a security perspective, Windows 8 is comparable to iOS, primarily due to the fact that apps need to be approved by Microsoft and downloaded via its dedicated store. (This applies to the Windows 8 RT version for now). Unlike Android, there is no requirement to install dedicated antivirus/anti-malware security software (though it would not hurt to do so).
Microsoft has seemingly finally listened to the constant criticism that Windows is not secure enough (and it is about time). Windows 8 will help keep users safer from malware and other security threats and supports some of the key security elements that iOS does (although there are many differences to each company’s approach). Microsoft supports the business market well with its Office suite, Exchange e-mail and related offerings, and has a large global set of customers who understand how its products work (including their shortcomings).
According to a recent a CNET article, “In one of the first independent tests of third-party security suites on Windows 8, nearly all antivirus and anti-malware software tested well. What may surprise you is that even without a third-party suite, Windows 8 is relatively resistant to modern threats like zero-day attacks.”
Did you ever think you would hear such a glowing report on Windows security? For any version? Ever?
Conclusion
Suffice it to say that as an Internet-enabled tablet user, you are always at risk but are able to mitigate much of the risk simply by avoiding risky situations as follows:
1. Do not jailbreak your tablet or smartphone. (If you are unfamiliar with this term, good.) This is the quickest and easiest way to break down your security and open yourself to cybercriminals. Apparently this issue has affected more Android tablets than iOS devices. (Windows 8 is kind of new to the tablet party, so it’s not worth mentioning).
2. If you use any Android or Windows device, be sure to download new apps from trusted sources only. Cybercriminals are known to contaminate web sites that offer free or pilfered popular apps (like Angry Birds), and many of these poached apps were infected with malicious code. Free is sometimes too high of a price to pay. Apple iPad owners can only download from the iTunes store, which offers a higher degree of safety since Apple ‘inspects’ all apps that apply for a listing here. While this is no guarantee that you will not experience any issues, at least it provides some peace of mind.
3. Always use passwords to protect access to your device. This offers some degree of protection of your data if the device is lost or stolen. Tracking is built in to Apple tablets by default, and in many Android tablets as well, so you will be able to not only locate your device, but also wipe its contents remotely in many instances.
Each of these tablet/OS families is quite good, and each stands on its merits in different market segments. At the risk of sounding like an Apple fan boy, the iPad remains the king of the hill for now in not only overall market share, but in securing your data as well.
 John Pawlicki is CEO and principal of OPM Research. He also works with Information Tool Designers (ITD), where he consults to the DOT’s Volpe Center, handling various technology and cyber security projects for the FAA and DHS. He managed and deployed various products over the years, including the launch of CertiPath (with world’s first commercial PKI bridge). John has also been part of industry efforts at the ATA/A4A, AIA and other industry groups, and was involved in the effort to define and allow the use of electronic FAA 8130-3 forms, as well as in defining digital identities with PKI. His recent publication, ‘Aerospace Marketplaces Report’ which analyzed third-party sites that support the trading of aircraft parts is available on OPMResearch.com as a PDF download, or a printed book version is available on Amazon.com.
John Pawlicki is CEO and principal of OPM Research. He also works with Information Tool Designers (ITD), where he consults to the DOT’s Volpe Center, handling various technology and cyber security projects for the FAA and DHS. He managed and deployed various products over the years, including the launch of CertiPath (with world’s first commercial PKI bridge). John has also been part of industry efforts at the ATA/A4A, AIA and other industry groups, and was involved in the effort to define and allow the use of electronic FAA 8130-3 forms, as well as in defining digital identities with PKI. His recent publication, ‘Aerospace Marketplaces Report’ which analyzed third-party sites that support the trading of aircraft parts is available on OPMResearch.com as a PDF download, or a printed book version is available on Amazon.com.
